Lab 4 is complete, and I’d probably give myself a passing grade for this round of questions. The subject this time was TCP SYN analysis. Now, if I were asked in an interview to “describe the TCP handshake” I’d have been able to answer that no problem. But the analysis and questions in this lab went a bit deeper than simply filtering for SYN, SYN/ACK, and ACK packets.
One of the early bits of learning in this lab was identifying Wireshark’s coloring scheme, what it means, and how to identify the color filters within the frame. I’m sure you knew that, but I didn’t. For instance:
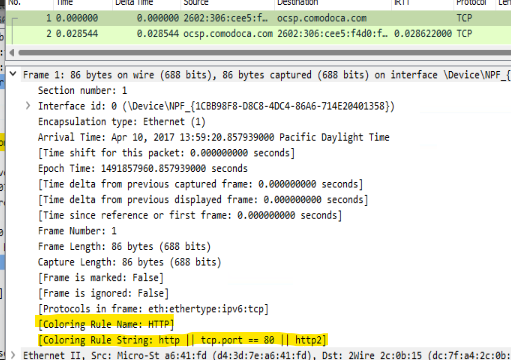
Here I simply thought green meant good. No, seriously. I didn’t want to Bing this answer, and my poking around didn’t lead me to the real answer, so when it came time for me to note something….
Yea…
There were a few questions that asked to identify how many TCP conversations contained certain flags or options. I missed quite a few of these, mostly due to how I had interpreted “conversations”.
We looked again at things like Window Scaling, Selective ACK, and Maximum Segment Size, with an interesting question around how communication would suffer if one of those weren’t set.
In some of these cases I wonder what the diagnostic or troubleshooting reason for finding these data point might be (such as locating sequence numbers), but I think the real goal for this early in the workbook is to get comfortable simply “finding information”. Certainly there’s an emphasis on finding and building filters.
The nice thing I’ve noticed with Wireshark is that there’s actually a lot of contextual help if you know where to look. For example:
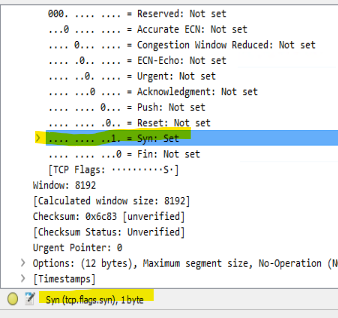
With the SYN: Set highlighted, you get the filter syntax at the bottom of the window. There’s tons of this sort of help.
These lab questions were definitely harder (for me) than the prior labs, but that’s what it’s all about — pushing myself, learning new things. More tools for the toolkit.